Introduction System Project Report
System Project Report is a basic device that helps both pupils and school bodies. Both operations have performed manually in the new setup. It takes a lot of time and is expensive. The different tasks relating to students have included in our student management system.
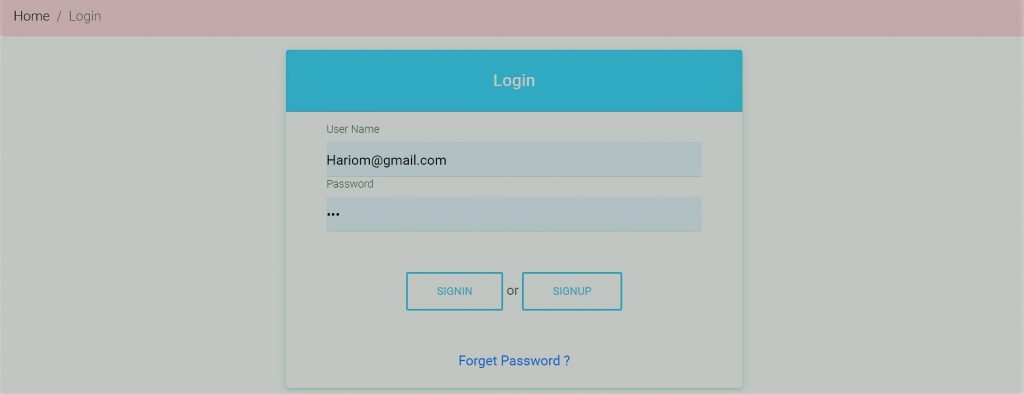
This program consists primarily of 3 modules.
Modulus user.
Module for students.
Module for Mark Management.
We will log in to the Software as a user and the user, student, and manager of two forms. The administrative administrator is able to install new users and can edit and uninstall an account. A student can register as a user, add and remove the profile of the student. The manager will apply markers for the student and remove them. The traces have used by all users.
System Analysis
System analytics has a systematic analysis of the different processes carried out inside. And beyond the system and its relationships. The main question here is. What are the current system’s problems?. To fix the dilemma. What must be done?.
In the course of the review of the results. The reports, decision points, and transactions handled by this method had gathered. Data flow diagrams, interviews, etc are the most common methods in the framework. For the collection of the relevant information necessary to create a method. Training, expertise, and common sense have required.
The study of systems can be classified into four parts.
Planning of system and initial inquiry.
Information collection. Information collection.
Apply standardized analytical tools.
Review of Facility.
Analysis of cost/benefit.
In the method, we already maintain a set of documents relating to the student. And want to manually input the student’s data and labels. In this scheme, the teacher or the school authority just looks at the student’s mark. And has to access the student’s information. It takes time and costs a great deal.
Proposed System
We are able to add the specifics of the students in our proposed scheme. The school authorities and teachers’ overhead is also decreasing. Another benefit of the scheme being that editing the student’s data. Deleting a student as considered to be unnecessary is quite simple. The student’s marks have included in the database. So that they can display their marks anytime they choose.
There are some benefits of our suggested scheme.
Pleasant interface for users.
Rapid client usage.
A slight mistake.
More space for storage.
Facilities for search.
Environmental Look and Feel.
Fast contract. Fast transaction.
The computerization has corrected all manual problems in handling student information at school or college.